Let’s encrypt is non-profit certificate authority managed by internet security research group (ISSR) that provides security at no cost. It uses protocol called automated certificate managed environment (ACME) that automates enrolling with the certificate authority. Let’s encrypt protocol enable setting of https server which automatically obtains the server without man intervention. This is achieved by running the management agent in the user agent. A client side software called certbot is installed which handles domain validation, order certificate, handle requests, installation of certificate and configures the https encryption in the server.
To set up a secure connection for domain trialEncrypt.com, for example involves two steps:
- Domain validation –here the agent proves that it control the a domain
- Certificate issuance and revocation –here the agent can request, revoke or renew SSL certificate.
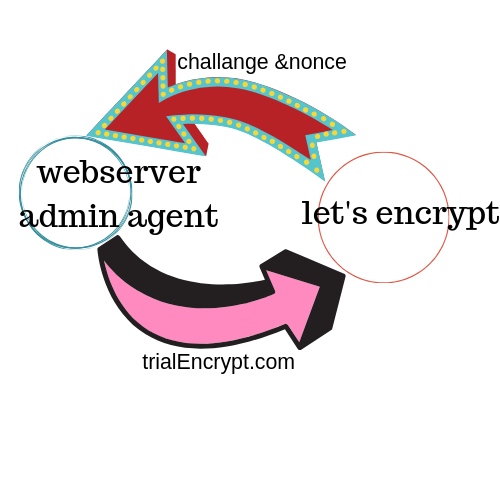
Domain validation
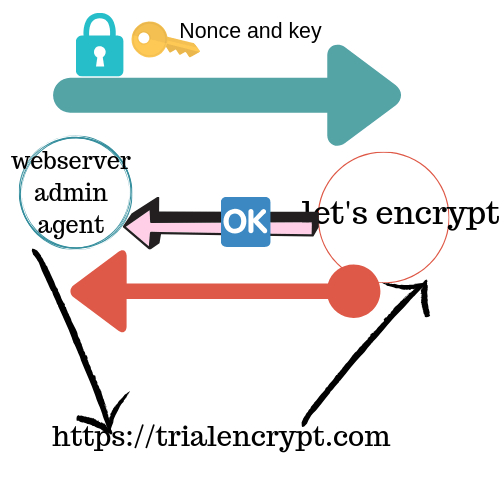
The agent generates the new key pair for the first time it tries to interact with let’s encrypt and proves the server control one of the domain which is the same process in the traditional Certificate authority. The agent and let’s encrypt undergo challenge-response to verify the agent controls the domain. The agent provides a nonce to the agent to sign with its private key to prove that it controls the key. The server web admin agent is identified by the public key.
When the agent is done with challenge and has signed the nonce, it notifies the CA that it’s ready to complete the validation. The nonce and the challenge are checked and if they are valid the agent identified by the public key is authorized to do certificate management for trialEncrypt.com.
Certificate issuance and Revocation.
The agent request for a certificate from let’s encrypt CA by sending a signed certificate signing request [signed with the authorized key for trialEncrypt.com] with specified public key. The CSR is signed with the private key corresponding to the public key in the CSR. When CA verifies all the details to be authentic, it sends the certificate with the public key to requesting agent for trialEncrypt.com. The resulting certificate is cached and you will not require validation until the 30 day period lapses.
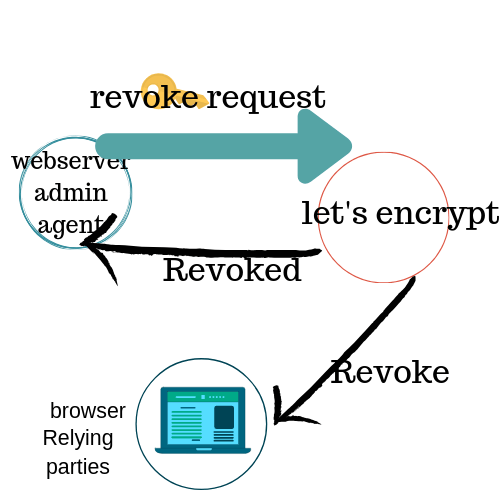
When revoking, the agent sends the revocation request to the CA and once verified the request is authorized and the all software that depend on this are notified.
Let’s encrypt certificate last for a period of 90 day after which you are required to renew.
